How to map tls-nsx-t certificate in TKGI to the certificate registered with NSX-T
What is the function of tls-nsx-t certificate?¶
tls-nsx-t certificate is created per cluster and registered with NSX-T during the cluster creation process. This certificate takes part in the communication between ncp process running on control plane VMs of the K8s cluster created by TKGI and NSX-T manager. This certificate when created during the cluster creation phase has a default expiration date of 2years from the date of cluster creation. The expiration of this certificate will cause communication between NCP and NSX-T manager to fail.
How to check the expiry of tls-nsx-t certificate?¶
In TKGI use the command below and replace the service-instance_7932956f-fcdc-4501-a136-b68a9f91f445 with the one from your environment.
credhub get -n /p-bosh/service-instance_7932956f-fcdc-4501-a136-b68a9f91f445/tls-nsx-t --output-json | \
jq '.value | .certificate' -r | \
openssl x509 -noout -text
There are few details that should be noted which will be used in later steps to map the certificate in NSX-T manager.

On the TKGI master nodes the certificate is present at /var/vcap/jobs/ncp/config/certs/nsx/client.crt. Use the following commands to view the details
How to map the certificate in NSX-T manager UI?¶
In NSX-T manager UI, navigate to System → Certificates → Certificates Tab and look for the Issued To and Issued By details. Check the entry which matches to Issuer and Subject highlighted in the previous screenshot. Click on the Certificate entry to verify the serial number.
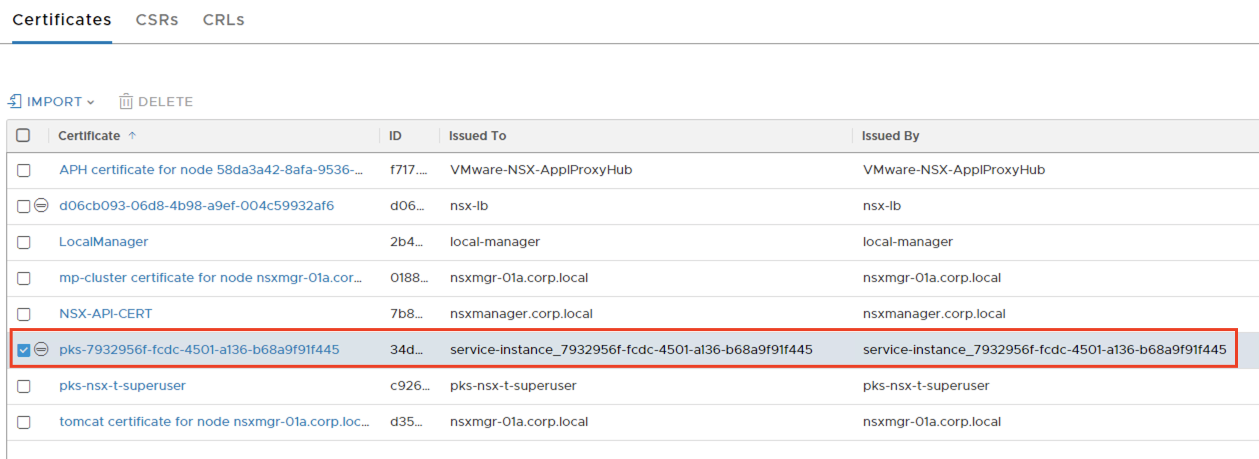
Check the serial number¶
As seen in the screenshot below Serial: 2a09279039f96ba57377afab1a84927f50a6698e in NSX-T manager matches to the Serial Number: 2a:09:27:90:39:f9:6b:a5:73:77:af:ab;1a:84:92:7f:50:a6:69:8e in the credhub output confirming the mapping. There are other highlighted details in the screenshot below which can also be mapped to the credhub output.
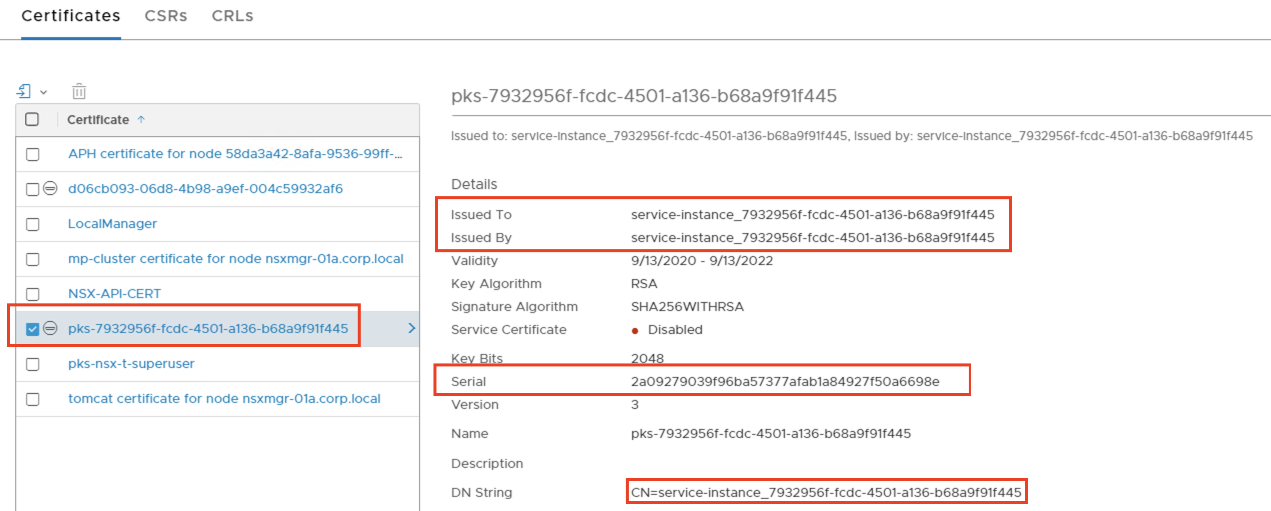
How to rotate tls-nsx-t certificate in TKGI?¶
I have covered in another post how to rotate this certificate manually. Please note that rotating in credhub alone is not sufficient, the certificate also needs to be registered with NSX-T and associated with the correct principal ID. The process in the other post covers those steps as well. Another important thing to note is that the new certificate won't be visible in the NSX-T manager UI with the same name(pks-xxx) as earlier but it will be a new UUID now. This is the same UUID that was earlier associated with the principal identity.
To confirm the new serial number use the below command on TKGI master VM after completing the certificate rotation procedure.